Exploring the Depths of Network Services: Nmap’s UDP Port Scanning
Related Articles: Exploring the Depths of Network Services: Nmap’s UDP Port Scanning
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Exploring the Depths of Network Services: Nmap’s UDP Port Scanning. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Exploring the Depths of Network Services: Nmap’s UDP Port Scanning
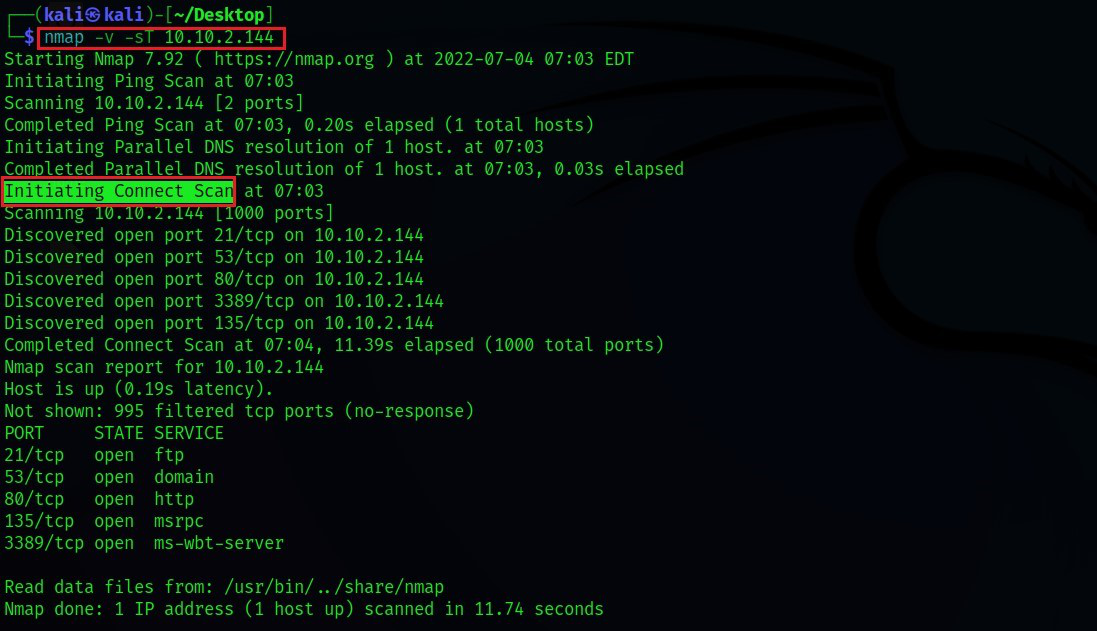
Network security professionals and system administrators rely on powerful tools to assess the vulnerabilities and functionalities of network devices. Among these tools, Nmap (Network Mapper) stands out as a versatile and indispensable tool for network discovery and security auditing. One of its key capabilities lies in its ability to scan for open UDP ports, a crucial aspect of understanding and securing network services.
Understanding UDP Ports and their Significance
The User Datagram Protocol (UDP) is a connectionless protocol used in network communication. Unlike its counterpart, TCP (Transmission Control Protocol), UDP does not establish a persistent connection between sender and receiver. This makes it suitable for applications that prioritize speed and efficiency over reliable data delivery, such as streaming media, online gaming, and DNS queries.
UDP ports, like their TCP counterparts, are numerical identifiers that associate specific applications or services with a network device. When a device receives a UDP packet, it analyzes the destination port number to determine which application should handle the incoming data.
Scanning UDP ports with Nmap provides valuable insights into a network’s configuration and potential vulnerabilities. By identifying open UDP ports, security professionals can:
- Discover active services: Open UDP ports indicate that a service is actively listening for incoming requests. This information helps in understanding the services running on a network device.
- Identify potential attack vectors: Malicious actors often exploit open UDP ports to launch attacks, such as denial-of-service (DoS) attacks or port scanning to identify vulnerable systems.
- Assess security posture: Knowing which UDP ports are open allows for a more comprehensive security assessment. By identifying unused or unnecessary services, administrators can reduce the attack surface and enhance security.
Nmap’s UDP Port Scanning Capabilities
Nmap offers a powerful suite of options for scanning UDP ports, enabling users to customize the scan to suit their specific needs.
Basic UDP Port Scanning:
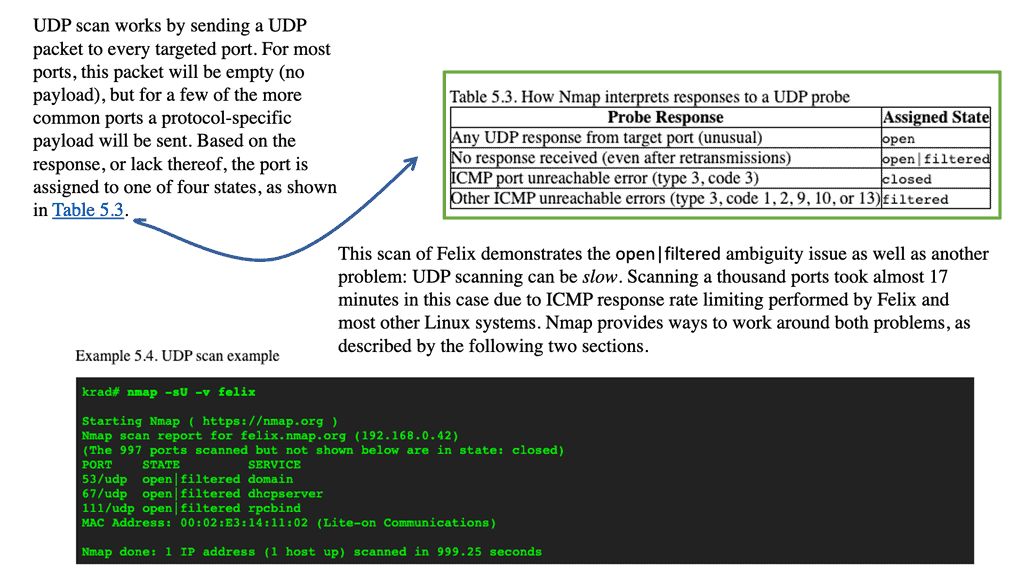
The simplest way to scan UDP ports is using the -sU flag. This flag tells Nmap to perform a UDP scan, attempting to connect to specified ports or a range of ports on the target device.
nmap -sU -p 53,123,500 192.168.1.100This command will scan ports 53, 123, and 500 on the target IP address 192.168.1.100 using UDP.
Advanced UDP Port Scanning Techniques:
Nmap offers several advanced techniques for UDP port scanning, providing greater control and flexibility.
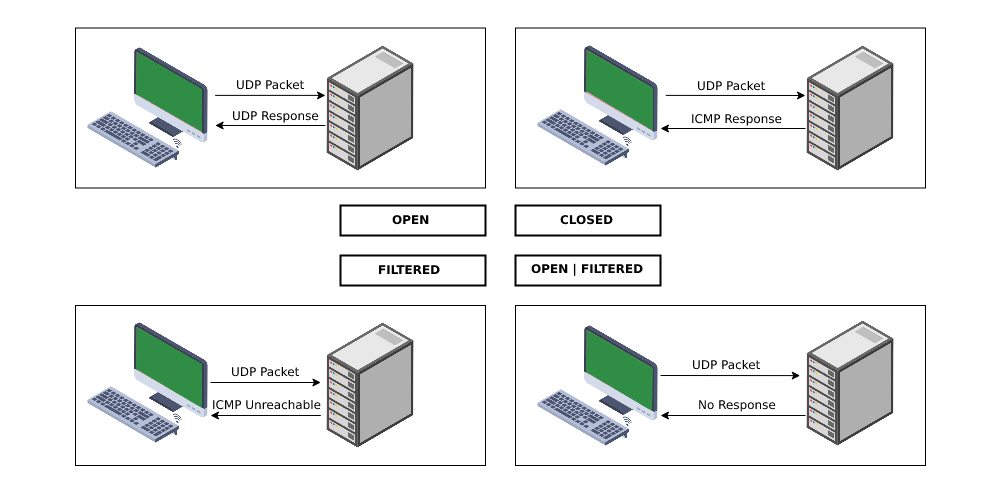
- UDP Connect Scan (-sU): This is the default UDP scan, sending a UDP packet to each port and waiting for a response. This method is suitable for identifying open ports that actively respond to requests.
- UDP SYN Scan (-sU): Similar to TCP SYN scan, this technique sends a SYN packet to each port. If the port is open, the target will send back a SYN-ACK packet, indicating the port is open.
- UDP ACK Scan (-sU): This scan sends an ACK packet to each port. If the port is open, the target will send back a RST (reset) packet.
- UDP Null Scan (-sU): This scan sends a null packet to each port. If the port is open, the target will send back a RST packet.
- UDP FIN Scan (-sU): This scan sends a FIN packet to each port. If the port is open, the target will send back a RST packet.
- UDP Xmas Scan (-sU): This scan sends a packet with the FIN, URG, and PSH flags set. If the port is open, the target will send back a RST packet.
Understanding Scan Results
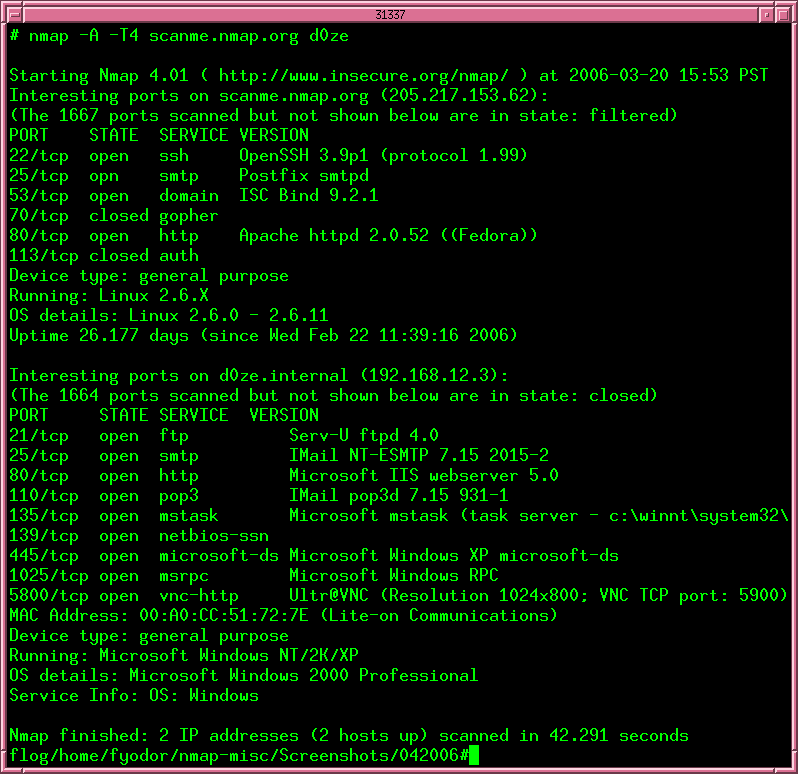
Nmap provides detailed information about the scanned ports, including:
- Port status: Open, closed, filtered, or unknown.
- Service name: If the port is open, Nmap attempts to identify the service running on that port.
- Version information: If the service is identifiable, Nmap may be able to determine the service version.
- Timing information: Time taken to scan each port.
Importance of UDP Port Scanning
Scanning UDP ports is crucial for several reasons:
- Security Assessment: It helps identify open ports that could be exploited by attackers, allowing for proactive security measures to be implemented.
- Service Discovery: It helps identify active services running on a network device, providing insights into the device’s functionality and configuration.
- Troubleshooting: It can help identify network connectivity issues related to UDP services.
- Compliance: Some security regulations and industry standards require regular UDP port scanning to ensure compliance.
FAQs Regarding Nmap’s UDP Port Scanning
Q: What is the difference between UDP and TCP port scanning?
A: TCP port scanning establishes a connection with the target device, while UDP port scanning sends packets to the target device and waits for a response. TCP scans are more reliable but can be slower, while UDP scans are faster but less reliable.
Q: Why is it important to scan UDP ports?
A: UDP ports are often used by critical services and can be exploited by attackers. Scanning UDP ports helps identify vulnerabilities and ensure network security.
Q: How do I scan specific UDP ports with Nmap?
A: You can use the -p flag followed by the port numbers or ranges. For example, nmap -sU -p 53,123,500 192.168.1.100 will scan ports 53, 123, and 500 on the target IP address 192.168.1.100.
Q: What are some common UDP services?
A: Common UDP services include DNS (Domain Name System), DHCP (Dynamic Host Configuration Protocol), and SNMP (Simple Network Management Protocol).
Q: How do I interpret Nmap’s UDP scan results?
A: Nmap’s output will display the port status (open, closed, filtered, or unknown), service name, version information, and timing information.
Tips for Effective UDP Port Scanning with Nmap
- Use appropriate scan techniques: Select the scan technique that best suits your needs, considering factors like speed, reliability, and potential for detection.
-
Customize scan parameters: Use flags like
-pto specify ports,-Tto adjust timing, and-Fto scan common ports. - Analyze scan results carefully: Pay attention to open ports, service names, and version information to identify potential vulnerabilities.
- Use Nmap scripts: Nmap’s scripting capabilities can automate complex scanning tasks and provide additional information.
- Combine with other tools: Integrate Nmap with other security tools for a more comprehensive security assessment.
Conclusion
Nmap’s UDP port scanning capabilities provide a powerful tool for network security professionals and system administrators. By understanding UDP ports and their significance, and by effectively utilizing Nmap’s options and techniques, organizations can proactively identify vulnerabilities, improve security posture, and ensure the integrity of their networks.





Closure
Thus, we hope this article has provided valuable insights into Exploring the Depths of Network Services: Nmap’s UDP Port Scanning. We appreciate your attention to our article. See you in our next article!
