Navigating the Complexities of Network Security: A Comprehensive Look at Map Testing 210
Related Articles: Navigating the Complexities of Network Security: A Comprehensive Look at Map Testing 210
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Navigating the Complexities of Network Security: A Comprehensive Look at Map Testing 210. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Complexities of Network Security: A Comprehensive Look at Map Testing 210

In the ever-evolving landscape of cybersecurity, where threats are constantly evolving and becoming increasingly sophisticated, ensuring network security is paramount. A crucial tool in this battle is Map Testing 210, a method employed to assess the security posture of a network by systematically probing its vulnerabilities and identifying potential weaknesses. This testing methodology, known for its rigor and effectiveness, serves as a critical element in bolstering network security and mitigating potential risks.
Understanding the Core of Map Testing 210
Map Testing 210, a comprehensive approach to network security assessment, goes beyond traditional vulnerability scanning. It employs a structured and methodical approach to uncover potential security gaps, prioritizing a deep understanding of the network’s architecture, its configurations, and the applications running within it. The process involves several key stages:
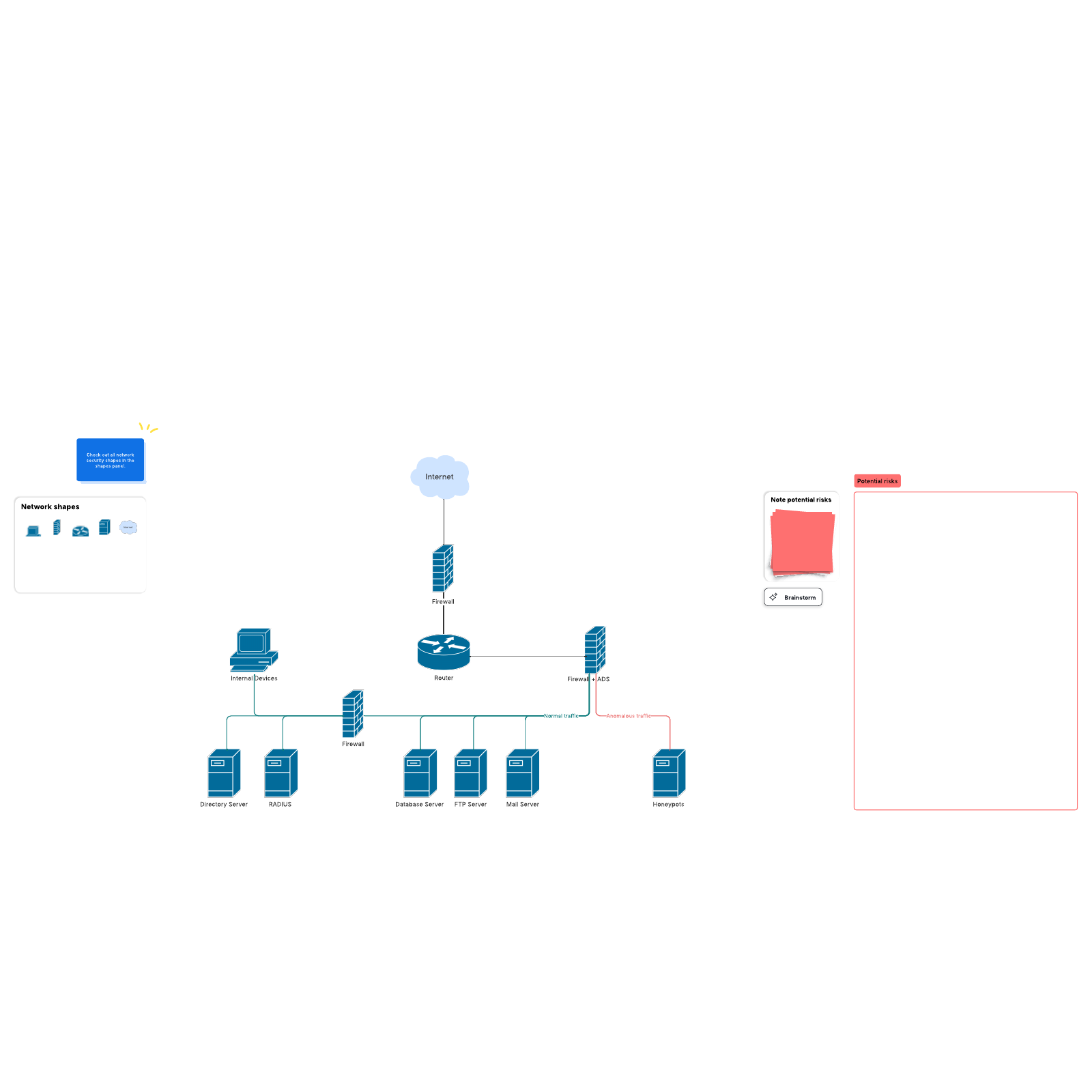
1. Network Discovery and Mapping: This initial phase involves meticulous identification and mapping of all network components, including devices, servers, applications, and their interconnections. This comprehensive inventory provides a foundational understanding of the network’s structure and its critical assets.
2. Vulnerability Scanning and Analysis: Once the network is thoroughly mapped, specialized tools are employed to scan for known vulnerabilities in operating systems, applications, and network devices. This stage leverages extensive vulnerability databases and exploits to identify potential weaknesses that could be exploited by malicious actors.
3. Penetration Testing: This phase simulates real-world attacks, employing techniques similar to those used by malicious actors to assess the network’s resilience. Penetration testing goes beyond vulnerability scanning, actively attempting to exploit identified vulnerabilities to gauge the effectiveness of security controls and the network’s overall security posture.
4. Reporting and Remediation: The final stage involves compiling a detailed report outlining identified vulnerabilities, their severity, potential impact, and recommended remediation steps. This report provides actionable insights to guide network administrators in prioritizing security improvements and implementing necessary countermeasures.
The Importance of Map Testing 210 in Modern Security Landscapes
The significance of Map Testing 210 in today’s digital world cannot be overstated. Its benefits extend far beyond simply identifying vulnerabilities; it empowers organizations to:
- Proactively Identify and Mitigate Risks: By uncovering potential weaknesses before malicious actors exploit them, Map Testing 210 helps organizations proactively address vulnerabilities, reducing the likelihood of successful attacks and minimizing potential damage.
- Enhance Security Posture: The comprehensive nature of the testing process allows organizations to gain a holistic understanding of their network’s security posture, enabling them to implement targeted improvements and strengthen their overall defense mechanisms.
- Comply with Regulatory Requirements: In many industries, regulatory compliance mandates regular security assessments. Map Testing 210 provides a robust framework for demonstrating compliance and meeting regulatory requirements.
- Improve Incident Response: By identifying and understanding vulnerabilities, Map Testing 210 facilitates the development of effective incident response plans. In the event of an attack, organizations can respond more effectively and efficiently, minimizing downtime and potential damage.
- Build a Culture of Security: The process of conducting Map Testing 210 can foster a culture of security within an organization, raising awareness of potential threats and encouraging a proactive approach to security.
Frequently Asked Questions about Map Testing 210
1. What are the different types of Map Testing 210?
Map Testing 210 can be tailored to specific needs and objectives. Common types include:
- Black Box Testing: This approach simulates an external attacker’s perspective, with no prior knowledge of the network’s internal structure.
- White Box Testing: This approach provides testers with detailed information about the network’s architecture, configurations, and applications, allowing for a more comprehensive assessment.
- Gray Box Testing: This approach combines elements of black box and white box testing, providing testers with limited information about the network.
2. How often should Map Testing 210 be conducted?
The frequency of Map Testing 210 depends on factors such as the organization’s size, criticality of its systems, and the evolving threat landscape. Generally, annual assessments are recommended, with more frequent testing for high-risk systems or in response to significant changes in the network environment.
3. What are the potential costs associated with Map Testing 210?
The cost of Map Testing 210 varies depending on the scope of the testing, the complexity of the network, and the expertise of the testing team. However, the cost should be considered an investment in security, as the potential financial and reputational damage caused by a successful attack far outweighs the cost of testing.
4. How can organizations ensure the effectiveness of Map Testing 210?
To ensure effectiveness, organizations should:
- Choose a reputable and experienced testing team: Partner with a team possessing the necessary skills and expertise to conduct comprehensive and thorough assessments.
- Clearly define the scope of the testing: Ensure that the testing covers all critical systems and applications within the network.
- Establish a clear reporting and remediation process: Clearly outline the reporting format and ensure that identified vulnerabilities are addressed promptly.
- Continuously monitor and adjust security controls: Regularly review and update security controls based on the findings of Map Testing 210 and the evolving threat landscape.
Tips for Implementing Effective Map Testing 210
- Involve key stakeholders: Ensure that key stakeholders, including IT staff, security personnel, and business leaders, are involved in the planning and execution of Map Testing 210.
- Prioritize vulnerabilities: Focus on addressing high-risk vulnerabilities first, taking into account their potential impact and likelihood of exploitation.
- Use automation tools: Leverage automated tools to streamline the testing process and enhance efficiency.
- Document findings and remediation steps: Maintain a comprehensive record of identified vulnerabilities and the remediation actions taken to address them.
- Regularly review and update testing procedures: As the threat landscape evolves, it’s essential to adapt testing procedures and methodologies to address emerging threats and vulnerabilities.
Conclusion: A Vital Tool for Network Security
Map Testing 210 is not just a security assessment; it’s a proactive approach to safeguarding networks and mitigating risks. By embracing this methodology, organizations can gain a deeper understanding of their security posture, identify potential vulnerabilities before they are exploited, and implement effective countermeasures to protect their critical assets. In today’s interconnected world, where cyberattacks are becoming increasingly prevalent, Map Testing 210 stands as a vital tool in the arsenal of network security professionals, enabling them to navigate the complexities of the digital landscape and ensure the safety and integrity of their organizations’ data and systems.






Closure
Thus, we hope this article has provided valuable insights into Navigating the Complexities of Network Security: A Comprehensive Look at Map Testing 210. We hope you find this article informative and beneficial. See you in our next article!