Unlocking the Secrets of Network Ports: A Comprehensive Guide to Nmap Port Scanning
Related Articles: Unlocking the Secrets of Network Ports: A Comprehensive Guide to Nmap Port Scanning
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unlocking the Secrets of Network Ports: A Comprehensive Guide to Nmap Port Scanning. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unlocking the Secrets of Network Ports: A Comprehensive Guide to Nmap Port Scanning

In the digital realm, networks are the arteries that carry information, and network ports act as the gateways through which data flows. Understanding the status and functionality of these ports is crucial for network administrators, security professionals, and anyone seeking to optimize network performance or identify potential vulnerabilities. This is where Nmap, a powerful and versatile network scanner, comes into play.
Nmap: A Network Explorer’s Toolkit
Nmap, short for Network Mapper, is a free and open-source network scanner widely used for network discovery, security auditing, and vulnerability assessment. Its primary function is to send packets to target systems and analyze the responses to gather information about their network status, open ports, and running services.
The Significance of Port Scanning
Port scanning using Nmap offers a multitude of benefits, including:
- Network Inventory and Mapping: Identifying all devices connected to a network, their IP addresses, and the services they offer. This information is essential for network management, troubleshooting, and planning.
- Security Auditing: Detecting open ports that could expose vulnerabilities to malicious actors. By identifying unneeded or misconfigured ports, security professionals can strengthen network defenses.
- Service Discovery: Discovering the services running on a network and their versions. This helps understand the network’s functionality, identify potential security risks, and plan for updates.
- Vulnerability Assessment: Identifying known vulnerabilities in running services based on their versions. This allows for proactive patching and mitigation of potential security threats.
- Troubleshooting Network Issues: Diagnosing network connectivity problems by identifying blocked or misconfigured ports.
Understanding Port Numbers
Ports are numerical identifiers that range from 0 to 65535. Each port is associated with a specific service or application running on a device. Ports are categorized into three main groups:
- Well-Known Ports (0-1023): These ports are reserved for standard services like HTTP (port 80), FTP (port 21), and SMTP (port 25).
- Registered Ports (1024-49151): These ports are assigned to specific services or applications by the Internet Assigned Numbers Authority (IANA).
- Dynamic or Private Ports (49152-65535): These ports are used by applications and services that require a temporary connection.
Nmap’s Arsenal of Scanning Techniques
Nmap offers a wide array of scanning techniques to suit various needs and security levels. Some of the most commonly used techniques include:
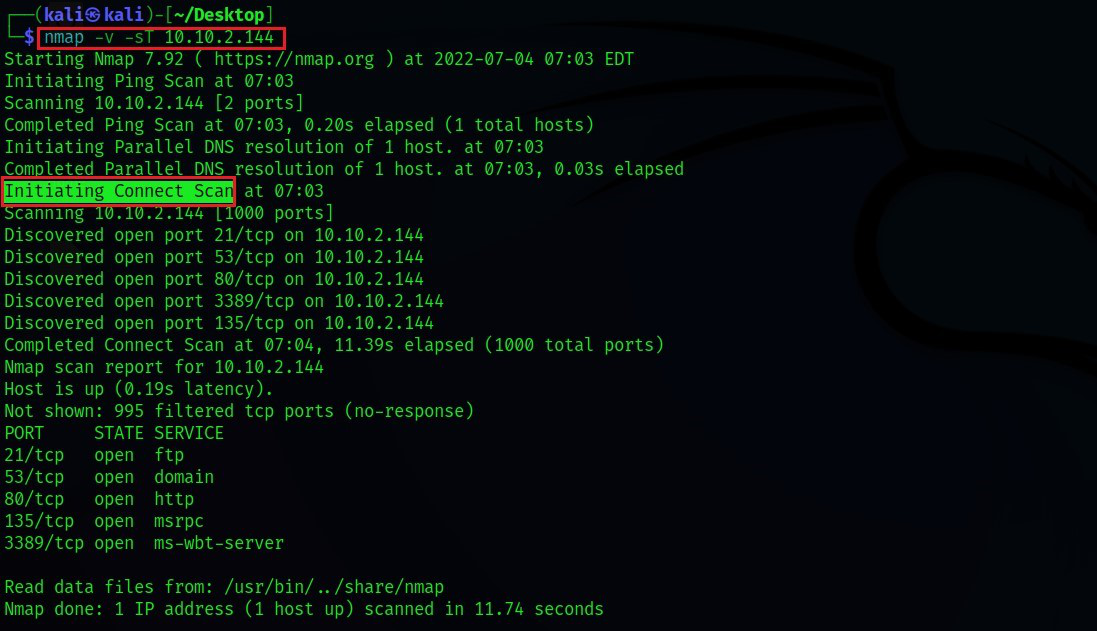
- TCP Connect Scan: This is the most basic scan, where Nmap attempts to establish a TCP connection to each port. A successful connection indicates an open port.
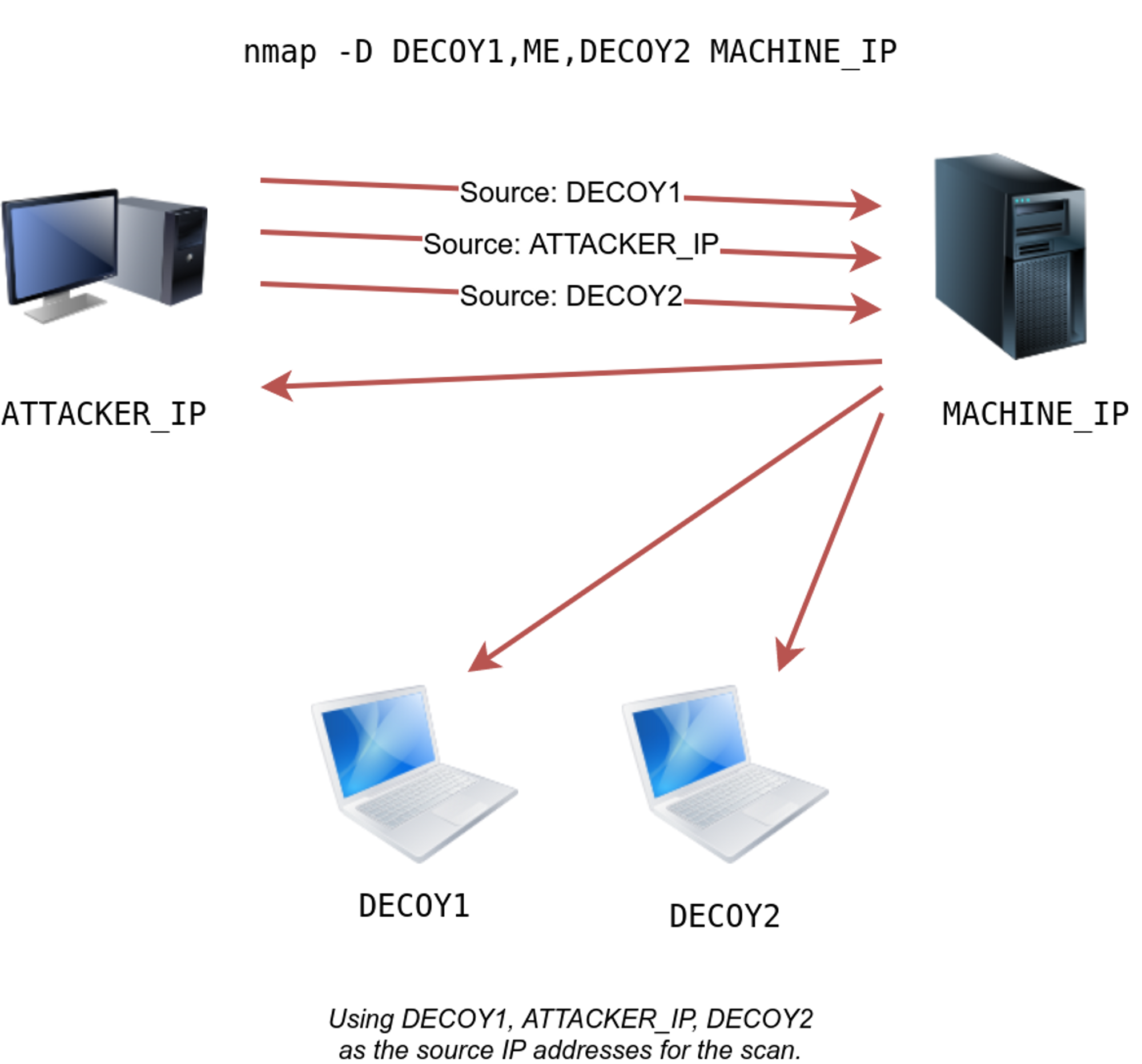
- SYN Scan (Half-Open Scan): This scan sends a SYN packet (the first step in a TCP handshake) to each port. If the target responds with a SYN-ACK, the port is open. This scan is stealthier than TCP Connect as it does not complete the connection.
- UDP Scan: This scan probes UDP ports by sending UDP packets. If the target responds with a UDP packet, the port is considered open.
- Ping Scan: This scan determines if a host is alive by sending ICMP echo requests. It doesn’t reveal open ports but can be used for initial network discovery.
- Version Scan: This scan attempts to identify the version of the service running on an open port. This information can be crucial for vulnerability assessment.
- OS Detection: Nmap can identify the operating system running on a target host by analyzing its responses to various probes.
Nmap’s Command-Line Interface: A Powerful Tool
Nmap’s command-line interface (CLI) provides a flexible and powerful way to perform scans and customize their behavior. Here are some common Nmap commands:
-
nmap -T4 -F <target>: Performs a fast scan using all common ports with a higher intensity level (T4). -
nmap -p 80,443 <target>: Scans only ports 80 and 443 (HTTP and HTTPS). -
nmap -sV <target>: Performs a version scan to identify the versions of running services. -
nmap -O <target>: Attempts to identify the operating system running on the target. -
nmap -sS <target>: Performs a SYN scan, which is stealthier than a TCP Connect scan. -
nmap -sU <target>: Performs a UDP scan to identify open UDP ports.
Nmap: More Than Just a Scanner
Nmap’s capabilities extend beyond basic port scanning. It offers advanced features like:
- Script Scanning: Nmap can execute scripts to perform more in-depth vulnerability assessments.
- Service Detection: Nmap can detect and identify running services, even those not listening on standard ports.
- Network Mapping: Nmap can map out entire networks, including their topology and device relationships.
- Customizability: Nmap’s scripting engine allows users to create and customize scripts for specific tasks.
Nmap in Action: Real-World Applications
Nmap is a valuable tool for various professionals and organizations:
- Network Administrators: Nmap helps administrators manage and monitor their networks, identify potential security threats, and troubleshoot connectivity issues.
- Security Professionals: Nmap is essential for vulnerability assessments, penetration testing, and identifying security weaknesses.
- Researchers: Nmap assists researchers in studying network behavior, analyzing network traffic, and developing security tools.
- Law Enforcement: Nmap can be used to identify and locate devices involved in criminal activities.
FAQs About Nmap Port Scanning
Q: Is Nmap legal to use?
A: Nmap is a legitimate tool for network exploration and security auditing. However, using it to scan systems without permission can be illegal. It is crucial to obtain consent from the owners of the target systems before performing scans.
Q: Is Nmap ethical to use?
A: Nmap is ethical when used responsibly and for legitimate purposes, such as network management, security auditing, and research. However, using it for malicious activities, such as hacking or denial-of-service attacks, is unethical and illegal.
Q: What are the risks of using Nmap?
A: Using Nmap incorrectly or without proper authorization can lead to legal repercussions. It is essential to understand the legal and ethical implications of port scanning and to obtain consent before scanning any system.
Q: How can I protect myself from Nmap scans?
A: You can protect your systems from Nmap scans by:
- Closing unnecessary ports: Only open ports that are essential for your services.
- Using a firewall: Configure your firewall to block incoming traffic from unknown sources.
- Implementing intrusion detection systems (IDS): IDS can detect and alert you to suspicious network activity, including Nmap scans.
Tips for Using Nmap Effectively
-
Start with a basic scan: Use the
-T4 -Fflag for a quick overview of open ports. - Focus on specific ports: Target specific ports relevant to your investigation.
-
Use stealthy scans: Employ SYN scans (
-sS) to minimize the impact on the target network. -
Identify the operating system: Use the
-Oflag to detect the target’s operating system for better vulnerability assessment. - Utilize scripting: Leverage Nmap’s scripting capabilities for automated tasks and advanced analysis.
Conclusion
Nmap is a powerful and versatile tool for network exploration and security auditing. By understanding its capabilities and using it responsibly, individuals and organizations can gain valuable insights into their networks, identify potential vulnerabilities, and enhance their overall security posture. Whether used for network management, security assessment, or research, Nmap remains an indispensable tool in the digital age.





Closure
Thus, we hope this article has provided valuable insights into Unlocking the Secrets of Network Ports: A Comprehensive Guide to Nmap Port Scanning. We hope you find this article informative and beneficial. See you in our next article!
