Unveiling Network Secrets: A Comprehensive Guide to Nmap
Related Articles: Unveiling Network Secrets: A Comprehensive Guide to Nmap
Introduction
With great pleasure, we will explore the intriguing topic related to Unveiling Network Secrets: A Comprehensive Guide to Nmap. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling Network Secrets: A Comprehensive Guide to Nmap

In the digital realm, where data flows through intricate networks, understanding the landscape of connected devices is paramount. This is where Nmap, a powerful and versatile network scanning tool, steps in. Nmap, short for Network Mapper, empowers security professionals, system administrators, and network engineers to gain valuable insights into network infrastructure, identify potential vulnerabilities, and optimize network performance.
This comprehensive guide delves into the intricacies of Nmap, exploring its capabilities, functionalities, and applications. We will navigate through its core features, unravel the underlying principles of network scanning, and illustrate practical use cases that demonstrate its immense value.
The Foundation of Network Exploration: Nmap’s Core Capabilities
Nmap’s versatility lies in its ability to perform a wide array of network scans, providing comprehensive information about network devices. Here are some of its key capabilities:
-
Host Discovery: Nmap excels at identifying active hosts on a network. It utilizes various techniques, including ping sweeps, SYN scans, and UDP probes, to detect devices that are responding to network traffic. This initial step lays the groundwork for further exploration.
-
Port Scanning: Once hosts are identified, Nmap can scan for open ports, revealing which services are listening on those ports. This information is crucial for understanding the services running on each device and identifying potential vulnerabilities.
-
Operating System Detection: Nmap can infer the operating system running on a target device by analyzing the responses it receives during port scans. This capability provides valuable context and aids in vulnerability assessments.
-
Service Version Detection: Nmap goes beyond identifying the service running on a port and can often determine the specific version of the service. This information is vital for pinpointing known vulnerabilities and selecting appropriate security measures.
-
Network Mapping: Nmap can visualize the topology of a network by mapping out the connections between devices. This graphical representation aids in understanding network layout and identifying potential bottlenecks.
Unraveling the Mysteries: Nmap’s Scanning Techniques
Nmap employs a diverse range of scanning techniques to gather information about network devices. Understanding these techniques is crucial for choosing the appropriate scan type for a specific task:
-
Ping Scan: This simple technique sends ICMP echo requests to target hosts. A response indicates that the host is reachable and likely active.
-
SYN Scan (Half-Open Scan): This scan, also known as a stealth scan, sends SYN packets to target ports. The scan concludes without establishing a full TCP connection, making it less detectable by intrusion detection systems.
-
Connect Scan: This scan establishes a full TCP connection to target ports, sending a SYN, ACK, and FIN sequence. While more detectable, it provides reliable information about open ports.
-
UDP Scan: Nmap can also scan for open UDP ports by sending UDP packets to target ports. This technique is often less effective than TCP scans due to the stateless nature of UDP.
-
FIN Scan: This scan sends FIN packets to target ports. The response received can indicate whether the port is open, closed, or filtered. This technique is less intrusive than other scans but may not be reliable in all situations.
-
Null Scan: This scan sends packets with all flags set to zero. The response received can indicate whether the port is open, closed, or filtered. This technique is less intrusive than other scans but may not be reliable in all situations.
-
Xmas Scan: This scan sends packets with the FIN, URG, and PSH flags set. The response received can indicate whether the port is open, closed, or filtered. This technique is less intrusive than other scans but may not be reliable in all situations.
-
Idle Scan: This scan leverages a technique known as IP ID Spoofing to determine open ports without directly interacting with the target host. This method minimizes detection but requires careful configuration.
-
Script Scanning: Nmap offers a vast library of scripts that automate various tasks, including service detection, vulnerability scanning, and network auditing. These scripts can significantly enhance the efficiency and effectiveness of network scans.
Practical Applications: Unveiling Nmap’s Power
Nmap’s capabilities extend far beyond basic network reconnaissance. Its applications are diverse, spanning security assessments, network administration, and even research. Here are some compelling use cases:
-
Security Auditing: Nmap is a cornerstone tool for security professionals. It enables them to identify open ports, vulnerable services, and potential attack vectors. This information is crucial for prioritizing security measures and mitigating risks.
-
Network Inventory Management: System administrators use Nmap to discover devices on their networks, identify their operating systems, and assess their configuration. This information helps maintain network security, optimize performance, and manage resources effectively.
-
Vulnerability Assessment: Nmap can be integrated with vulnerability databases and scanners to automatically identify known vulnerabilities in network devices. This proactive approach allows for timely patching and mitigation of risks.
-
Network Troubleshooting: Nmap helps troubleshoot network connectivity issues by identifying devices that are not responding or experiencing communication problems. Its ability to map network topology also assists in pinpointing network bottlenecks.
-
Research and Development: Nmap is used by security researchers to study network protocols, analyze malware behavior, and develop new security tools and techniques. Its versatility makes it an invaluable resource for pushing the boundaries of network security.
Nmap in Action: A Step-by-Step Guide
To illustrate Nmap’s power, let’s consider a practical scenario:
Objective: Identify all active hosts on a network and determine the services running on those hosts.
Steps:
-
Install Nmap: Nmap is available for various operating systems, including Linux, Windows, and macOS. Download and install the appropriate version for your system.
-
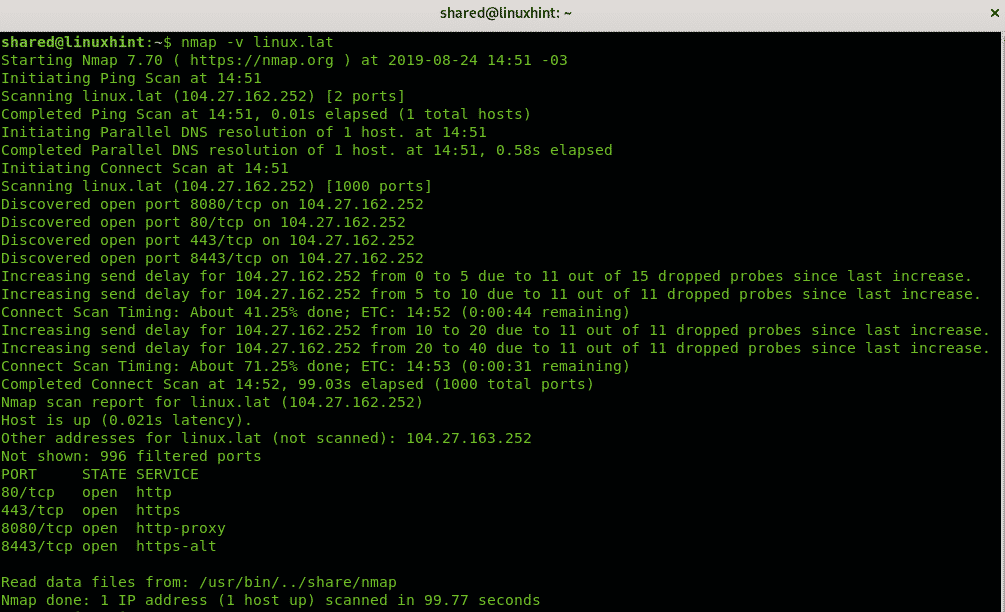
Run a Host Discovery Scan: Execute the following command in a terminal:
nmap -sn 192.168.1.0/24This command performs a ping scan on the network subnet 192.168.1.0/24, identifying all active hosts.
- Run a Port Scan: Once hosts are identified, use the following command to scan for open ports on a specific host:
nmap -T4 -p- 192.168.1.10This command performs a comprehensive port scan on the host with IP address 192.168.1.10, scanning all ports and using aggressive timing options for faster results.
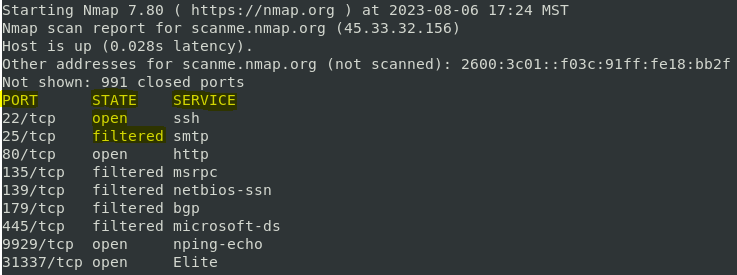
- Analyze the Output: Nmap provides detailed output, including the host’s IP address, MAC address, operating system, and the services running on open ports.
Interpreting the Output:
The output of Nmap scans provides valuable insights into the network. Understanding the information presented is crucial for effective analysis:
-
Host Status: Nmap indicates whether a host is up or down, based on its response to network probes.
-
Port Status: Nmap classifies ports as open, closed, filtered, or unknown, depending on the responses received.
-
Service Information: Nmap identifies the service running on each open port and often provides the service version.
-
Operating System Detection: Nmap attempts to identify the operating system running on each host, based on its responses to network probes.
-
Network Topology: Nmap can generate a graphical representation of the network, highlighting connections between devices and providing insights into network layout.
FAQs: Addressing Common Queries
1. Is Nmap Legal to Use?
Nmap is a legitimate tool and its use is generally legal. However, it’s crucial to adhere to ethical hacking principles and respect network security policies.
2. Can Nmap be Used for Malicious Activities?
While Nmap is a powerful tool, it can be misused for malicious purposes. It’s essential to use it responsibly and ethically, adhering to legal and ethical guidelines.
3. How Secure is Nmap Itself?
Nmap is a robust tool with a strong security track record. However, it’s crucial to keep it updated with the latest security patches to mitigate potential vulnerabilities.
4. Can Nmap be Detected by Firewalls or Intrusion Detection Systems (IDS)?
Some Nmap scan techniques, such as SYN scans, are designed to be stealthy and less detectable. However, advanced firewalls and IDS can still detect Nmap activity.
5. What are the Best Practices for Using Nmap?
- Obtain Permission: Always obtain permission before scanning a network.
- Use Specific Scans: Choose the appropriate scan type for your task.
- Limit Scan Scope: Focus on specific hosts or subnets.
- Use Timing Options: Adjust scan speed to minimize network impact.
- Analyze Output Carefully: Interpret Nmap output thoroughly.
Tips for Effective Nmap Utilization
- Start with Basic Scans: Begin with simple scans to gather initial information.
- Use Scripting Capabilities: Leverage Nmap’s script library to automate tasks.
- Combine with Other Tools: Integrate Nmap with other security tools for comprehensive assessments.
- Stay Updated: Keep Nmap and its scripts updated for optimal performance.
- Document Your Findings: Record scan results for future reference.
Conclusion: Embracing the Power of Nmap
Nmap is an indispensable tool for network professionals, security researchers, and anyone seeking to gain a deeper understanding of network infrastructure. Its versatility, power, and wide range of applications make it a valuable asset for security assessments, network administration, and research. By mastering Nmap’s capabilities and adhering to ethical guidelines, users can leverage its power to enhance network security, optimize performance, and uncover the hidden secrets of the digital landscape.





Closure
Thus, we hope this article has provided valuable insights into Unveiling Network Secrets: A Comprehensive Guide to Nmap. We hope you find this article informative and beneficial. See you in our next article!
