Unveiling Network Secrets: A Comprehensive Guide to Nmap Scanning
Related Articles: Unveiling Network Secrets: A Comprehensive Guide to Nmap Scanning
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling Network Secrets: A Comprehensive Guide to Nmap Scanning. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unveiling Network Secrets: A Comprehensive Guide to Nmap Scanning
- 2 Introduction
- 3 Unveiling Network Secrets: A Comprehensive Guide to Nmap Scanning
- 3.1 Understanding Nmap’s Capabilities
- 3.2 Nmap’s Diverse Applications
- 3.3 Essential Nmap Commands and Techniques
- 3.4 Nmap’s Advantages and Limitations
- 3.5 Nmap Testing Site: A Practical Learning Environment
- 3.6 FAQs About Nmap Testing Sites
- 3.7 Tips for Using Nmap Testing Sites
- 3.8 Conclusion
- 4 Closure
Unveiling Network Secrets: A Comprehensive Guide to Nmap Scanning
Nmap, short for Network Mapper, is a powerful and versatile tool that has become indispensable for network administrators, security researchers, and penetration testers. Its ability to scan networks and gather information about devices, services, and vulnerabilities makes it a cornerstone of network security assessments and troubleshooting. This article provides a comprehensive exploration of Nmap, delving into its capabilities, applications, and the significance it holds in today’s interconnected world.
Understanding Nmap’s Capabilities
At its core, Nmap is a network scanner that utilizes various techniques to probe networks and gather information. Its primary functions include:
- Host Discovery: Identifying active hosts on a network by sending packets and analyzing responses. Nmap can detect hosts even if they are not actively communicating.
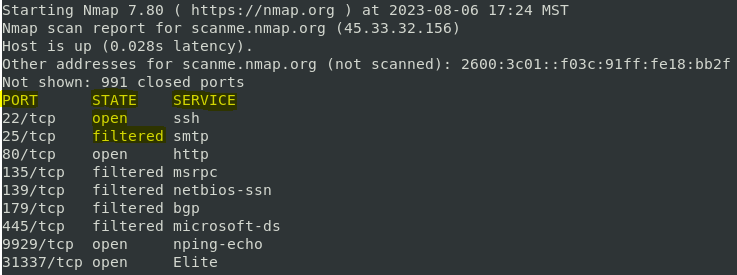
- Port Scanning: Identifying open ports on discovered hosts and determining the services running on those ports. This reveals potential vulnerabilities and provides insights into the network’s services.
- Operating System Detection: Identifying the operating system running on a host based on its responses to specific network probes. This knowledge is crucial for targeted attacks and vulnerability assessments.
- Service Version Detection: Determining the specific versions of services running on open ports. This allows for the identification of known vulnerabilities and outdated software.
- Network Mapping: Creating a visual representation of the network topology, including hosts, connections, and services. This provides a clear picture of the network’s structure and potential security risks.
Nmap’s Diverse Applications
Nmap’s versatility makes it a valuable tool across various domains:
- Network Security Assessment: Nmap is essential for identifying potential vulnerabilities, misconfigured services, and unauthorized devices on a network. This information helps security professionals prioritize remediation efforts and strengthen network defenses.
- Penetration Testing: Ethical hackers use Nmap to simulate real-world attacks and assess the security posture of systems and networks. This helps identify weaknesses and vulnerabilities before malicious actors exploit them.
- Network Troubleshooting: Nmap can help diagnose network connectivity issues by identifying unreachable hosts, blocked ports, and faulty network devices. This expedites troubleshooting and ensures network stability.
- Network Inventory Management: Nmap assists in creating a comprehensive inventory of network devices, their services, and configurations. This information is vital for network management and resource allocation.
- Research and Development: Researchers use Nmap to analyze network traffic patterns, identify emerging threats, and develop new security solutions. Its capabilities contribute to the advancement of cybersecurity knowledge.
Essential Nmap Commands and Techniques
Nmap offers a wide range of commands and techniques to perform various network scans. Here are some of the most commonly used:
-
Basic Scan:
nmap <target>- This command performs a simple scan of the specified target, identifying active hosts and open ports.
-
Port Scan:
nmap -p <port range> <target>- This command scans a specific range of ports on the target host.
-
Operating System Detection:
nmap -O <target>- This command attempts to identify the operating system running on the target host.
-
Service Version Detection:
nmap -sV <target>- This command identifies the versions of services running on open ports.
-
Stealth Scan:
nmap -sS <target>- This command performs a stealth scan, minimizing the chances of detection by firewalls.
-
SYN Scan:
nmap -sT <target>- This command performs a SYN scan, commonly used for bypassing firewalls.
-
UDP Scan:
nmap -sU <target>- This command scans UDP ports on the target host.
-
Ping Scan:
nmap -sP <target>- This command performs a ping scan, identifying active hosts on the network.
-
Script Scanning:
nmap --script=<script name> <target>- This command runs Nmap scripts to perform specific tasks, such as vulnerability checks or service identification.
Nmap’s Advantages and Limitations
Nmap offers numerous advantages, making it a preferred choice for network scanning:
- Versatility: Nmap’s wide range of features and capabilities cater to diverse needs, from basic network discovery to advanced vulnerability assessments.
- Open Source: Nmap’s open-source nature allows for free access, customization, and community contributions.
- Cross-Platform Compatibility: Nmap runs on various operating systems, including Windows, Linux, and macOS, ensuring widespread accessibility.
- Extensive Documentation: Nmap’s comprehensive documentation provides detailed explanations of its commands, features, and best practices.
- Active Community: A vibrant community of users and developers actively contributes to Nmap’s development, providing support, resources, and new features.
Despite its advantages, Nmap has certain limitations:
- Potential for Abuse: Nmap’s powerful capabilities can be misused for malicious purposes, such as conducting denial-of-service attacks or scanning for vulnerabilities.
- Firewall Detection: Some firewalls can detect and block Nmap scans, hindering its effectiveness.
- Limited Scope: Nmap primarily focuses on network scanning and may not provide comprehensive security assessments.
- Complexity: Nmap’s advanced features can be complex to use, requiring technical expertise and understanding.
Nmap Testing Site: A Practical Learning Environment
Nmap testing sites provide a safe and controlled environment for users to practice Nmap skills and explore its capabilities without affecting live networks. These sites typically offer:
- Virtualized Networks: Simulating real-world network environments with various devices, services, and vulnerabilities.
- Pre-configured Targets: Providing specific targets with known vulnerabilities and configurations for testing Nmap techniques.
- Interactive Tutorials: Offering step-by-step guidance on using Nmap commands and techniques for various scenarios.
- Feedback and Analytics: Providing insights into the effectiveness of scans and highlighting areas for improvement.
FAQs About Nmap Testing Sites
Q: Are Nmap testing sites legal to use?
A: Yes, Nmap testing sites are legal to use as long as they are explicitly designed for educational and testing purposes. They provide a safe and controlled environment for practicing network scanning techniques.
Q: What are the benefits of using Nmap testing sites?
A: Nmap testing sites offer numerous benefits, including:
- Safe Practice Environment: Allows users to practice Nmap skills without affecting live networks.
- Hands-On Learning: Provides practical experience with Nmap commands and techniques.
- Ethical Exploration: Enables users to experiment with different scanning methods and vulnerabilities in a controlled setting.
- Improved Understanding: Deepens understanding of network security concepts and Nmap’s capabilities.
Q: How do I find reputable Nmap testing sites?
A: Several reputable Nmap testing sites are available online. Look for sites that are:
- Clearly labeled as testing environments.
- Developed by trusted organizations or individuals.
- Provide comprehensive documentation and support.
- Offer a variety of scenarios and targets for testing.
Q: Are there any risks associated with using Nmap testing sites?
A: While Nmap testing sites are generally safe, there are potential risks:
- Malicious Actors: Some sites may be compromised or used by malicious actors to gather information or launch attacks.
- Data Privacy: Ensure that the testing site complies with data privacy regulations and handles user data responsibly.
- Unintended Consequences: Be aware of the potential impact of scans on the virtual network and its services.
Tips for Using Nmap Testing Sites
- Start with Basic Scans: Begin by practicing basic Nmap commands and gradually explore more advanced techniques.
- Read the Documentation: Familiarize yourself with the specific rules and guidelines of the testing site.
- Focus on Learning: Use the testing site as an opportunity to gain practical experience and deepen your understanding of Nmap.
- Respect the Environment: Avoid excessive or disruptive scans that could impact other users.
- Seek Help When Needed: Don’t hesitate to reach out to the testing site’s community or resources for assistance.
Conclusion
Nmap stands as a powerful and versatile tool for network administrators, security researchers, and penetration testers. Its ability to scan networks and gather information about devices, services, and vulnerabilities makes it a cornerstone of network security assessments and troubleshooting. Utilizing Nmap testing sites provides a safe and controlled environment for practicing Nmap skills and exploring its capabilities without affecting live networks. By embracing Nmap and its testing resources, individuals can enhance their network security knowledge and contribute to a more secure digital landscape.





Closure
Thus, we hope this article has provided valuable insights into Unveiling Network Secrets: A Comprehensive Guide to Nmap Scanning. We thank you for taking the time to read this article. See you in our next article!

