Unveiling the Secrets of Network Ports: A Comprehensive Guide to Nmap TCP Port Scanning
Related Articles: Unveiling the Secrets of Network Ports: A Comprehensive Guide to Nmap TCP Port Scanning
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling the Secrets of Network Ports: A Comprehensive Guide to Nmap TCP Port Scanning. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Secrets of Network Ports: A Comprehensive Guide to Nmap TCP Port Scanning

In the intricate world of computer networks, each device communicates through specific channels known as ports. These ports, numbered from 0 to 65535, act as virtual gateways, allowing applications and services to exchange data. Understanding which ports are open and what services they host is crucial for various tasks, ranging from network administration to security assessments.
This is where Nmap, the ubiquitous network scanner, steps in. Nmap’s powerful capabilities allow users to probe networks, identify active hosts, and map out the ports they expose. This information is invaluable for network administrators seeking to optimize performance, security professionals striving to identify vulnerabilities, and even researchers delving into the depths of network behavior.
The Essence of Nmap TCP Port Scanning
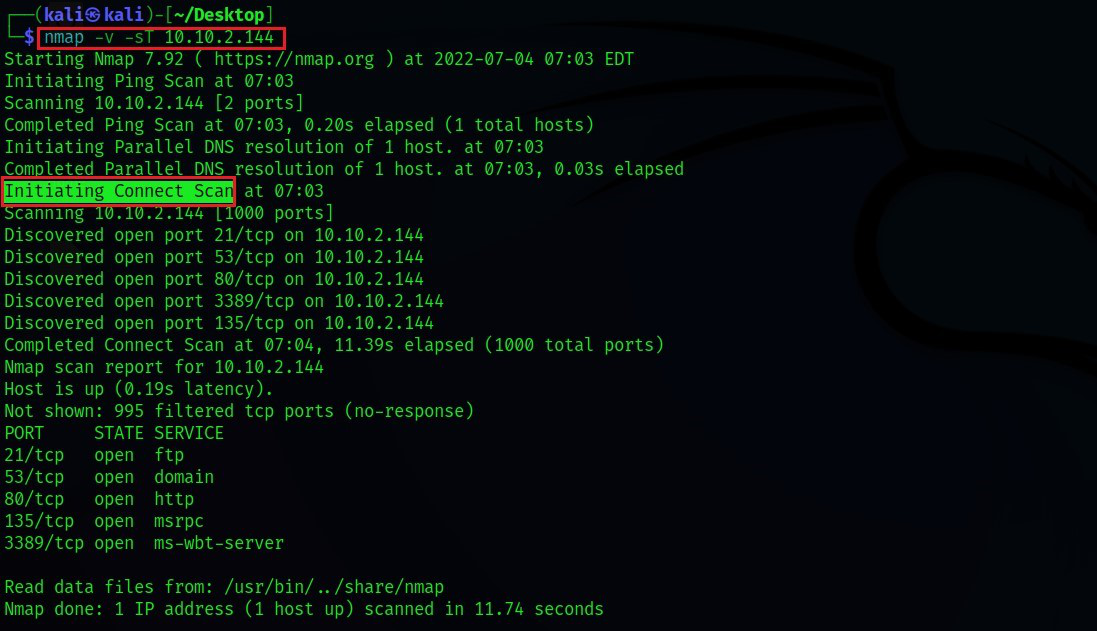
Nmap’s core function revolves around sending specially crafted packets to target systems and analyzing the responses. These packets, designed to interact with specific ports, reveal the state of the port:
- Open: The port is actively listening for connections, indicating a service is running.
- Closed: The port is not listening for connections, suggesting it’s not in use.
- Filtered: The port is blocked by a firewall or other security mechanism, preventing access.
By meticulously examining the responses, Nmap builds a detailed portrait of the network, outlining the ports in use and the potential services running on each. This information is presented in a concise and readable format, empowering users to make informed decisions about their network infrastructure.
Beyond Simple Port Identification: Unveiling the Potential
Nmap’s capabilities extend far beyond merely identifying open ports. Its versatility allows users to perform a multitude of tasks, including:
- Service Version Detection: Nmap can determine the specific service running on an open port, such as Apache web server or SSH daemon. This information is crucial for identifying potential vulnerabilities and tailoring security measures.
- Operating System Fingerprinting: Nmap can analyze network traffic patterns to infer the operating system running on a target device. This knowledge is invaluable for understanding the security posture of a system and tailoring attacks or defenses accordingly.
- Network Mapping: Nmap can be used to scan entire networks, identifying all active hosts and their associated ports. This information is critical for network administrators seeking to optimize network performance and security.
- Vulnerability Scanning: Nmap can be used to identify known vulnerabilities in services running on open ports. This information is essential for security professionals seeking to mitigate risks and protect sensitive data.
Understanding the Power of Nmap TCP Port Scanning
The value of Nmap TCP port scanning lies in its ability to provide a comprehensive view of network infrastructure, revealing insights that would otherwise remain hidden. This information is essential for:
- Network Administrators: Nmap helps administrators gain a clear understanding of their network topology, identify potential bottlenecks, and optimize performance.
- Security Professionals: Nmap allows security professionals to identify potential vulnerabilities, prioritize security measures, and assess the overall security posture of their network.
- Researchers: Nmap provides researchers with a powerful tool for studying network behavior, analyzing security trends, and developing new security solutions.
FAQs Regarding Nmap TCP Port Scanning
1. What are the ethical implications of Nmap TCP port scanning?
Nmap is a powerful tool, and its use must be aligned with ethical considerations. It’s crucial to respect the privacy of others and avoid scanning networks without permission. Nmap should only be used for legitimate purposes, such as network administration or security assessments.
2. How can I protect my network from Nmap scans?
While it’s impossible to completely prevent Nmap scans, there are several strategies to mitigate their impact:
- Firewall Configuration: Configuring firewalls to block unwanted traffic, including Nmap scans, can significantly reduce the risk of unauthorized access.
- Port Blocking: Closing unnecessary ports can limit the attack surface and reduce the potential for exploitation.
- Intrusion Detection Systems (IDS): Implementing IDS solutions can detect suspicious activity, including Nmap scans, and trigger appropriate responses.
3. What are some common Nmap commands for TCP port scanning?
-
nmap -T4 -F <target_ip>: This command performs a fast scan, identifying open ports on the target IP address. -
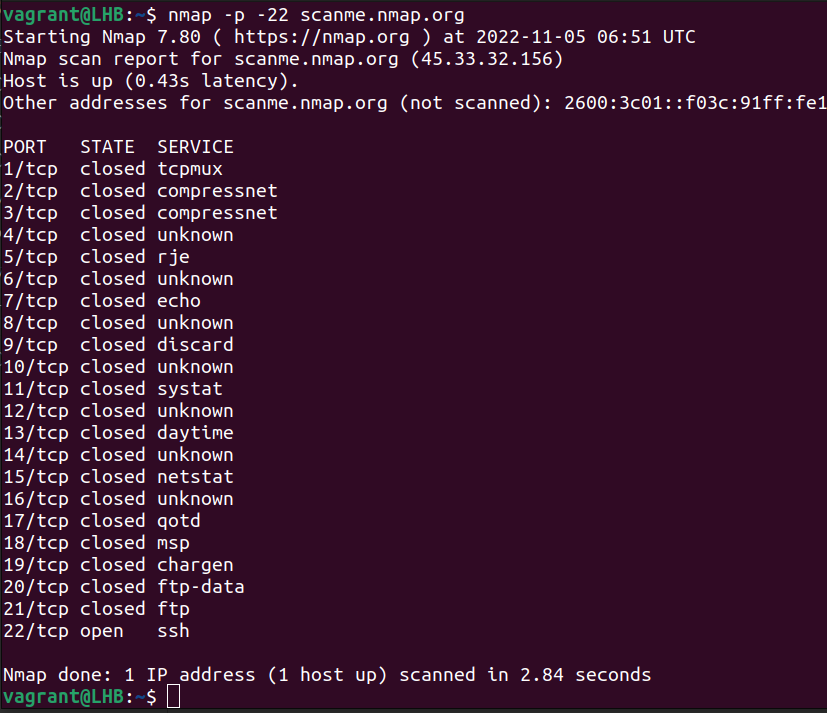
nmap -sS -p 22,80,443 <target_ip>: This command performs a SYN scan, focusing on specific ports (22, 80, and 443) and identifying their state. -
nmap -sV -p 80 <target_ip>: This command performs a version scan, identifying the service running on port 80 and its version.
4. What are some advanced Nmap techniques for TCP port scanning?
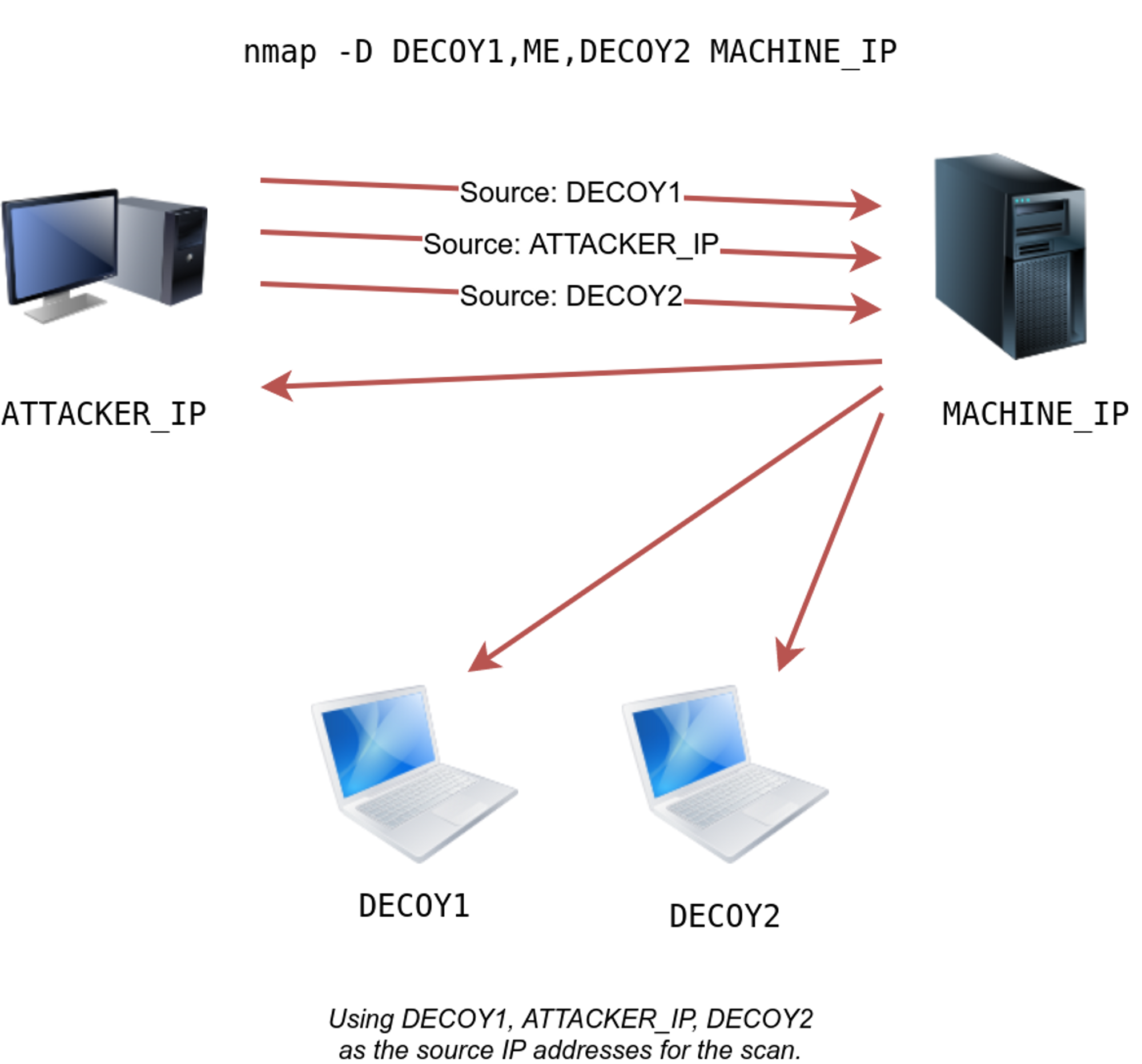
- Stealth Scans: Nmap offers stealth scan options that minimize the chance of detection by firewalls and intrusion detection systems.
- Script Scanning: Nmap can execute scripts to perform more complex tasks, such as identifying specific vulnerabilities or gathering detailed information about services.
- Exploitation: While Nmap is not primarily designed for exploitation, it can be used to test known vulnerabilities and assess the potential impact of attacks.
Tips for Effective Nmap TCP Port Scanning
- Start with Basic Scans: Begin with simple scans to gain a general understanding of the target network before moving on to more advanced techniques.
- Customize Scan Parameters: Adjust scan options based on your specific needs and the target network.
- Use Scripting for Automation: Automate repetitive tasks using Nmap scripting, saving time and effort.
- Consult Documentation: Refer to the Nmap documentation for detailed information on its capabilities and usage.
Conclusion
Nmap TCP port scanning is a powerful tool for network administrators, security professionals, and researchers alike. By providing a comprehensive understanding of network infrastructure, Nmap empowers users to optimize performance, identify vulnerabilities, and make informed decisions about their network security.
However, it’s crucial to use Nmap responsibly, respecting the privacy of others and adhering to ethical guidelines. With careful consideration and responsible usage, Nmap can be a valuable asset for any individual or organization seeking to manage and secure their network environment.




Closure
Thus, we hope this article has provided valuable insights into Unveiling the Secrets of Network Ports: A Comprehensive Guide to Nmap TCP Port Scanning. We thank you for taking the time to read this article. See you in our next article!
